Zero-Knowledge Proofs (ZPK) are a type of cryptographic algorithm, used in DeFi, that allows a person to prove that he/she possesses certain information, without revealing the information itself. In other words, it is a proof that allows to prove knowledge of a fact without having to reveal the content of that knowledge.
One of the most common examples of the use of Zero-Knowledge Proofs is in online identity verification. For example, if someone wants to access a bank account online, they may have to provide personal information, such as their national insurance number or date of birth. However, these pieces of personal information are highly confidential and their disclosure can be dangerous if they fall into the wrong hands. By using Zero-Knowledge Proofs, it is possible to prove that the information is known without having to disclose it, which improves the security of the identity verification process.
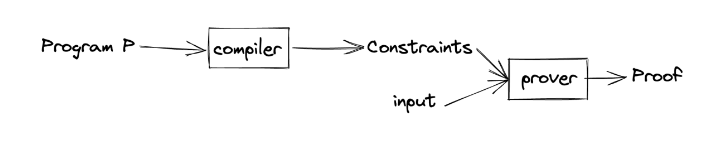
Another example of the use of Zero-Knowledge Proofs is in the verification of the execution of programs without revealing information about them. In the example mentioned above, one could prove that one knows the input of a program and is therefore able to obtain the desired response. This test could be useful, for example, in verifying the execution of programs in environments where information is highly confidential, and you do not want it to be disclosed.
DeFi & Zero-Knowledge Proofs
Decentralised finance (DeFi) has become a hot topic in the world of cryptocurrencies and blockchain. In short, DeFi refers to decentralized financial systems that use blockchain technology to enable financial transactions and activities without the need for traditional intermediaries, such as banks and stockbrokers.
In this context, zero-knowledge proofs (ZKPs) can play an important role in enhancing the privacy and security of financial transactions and activities in DeFi systems. ZKPs make it possible to prove that information is possessed or an action has been taken without revealing specific details about that information or action. For example, a user of a DeFi system could use a ZKP to prove ownership of a certain amount of cryptocurrency without having to disclose the exact amount. Similarly, a user could prove that he or she has made a transaction without revealing specific details about the transaction, such as the sender and recipient.
In addition to improving privacy and security, ZKPs can also help improve the efficiency of DeFi systems. By allowing users to test without having to interact with other users, ZKPs can reduce the number of transactions required to complete an action or transaction. This can speed up the time required to complete a financial activity on a DeFi system.
As DeFi systems continue to gain popularity, we are likely to see an increase in the use of ZKPs to improve the privacy, security, and efficiency of these platforms.
Non-interactive Zero-Knowledge Proofss (NIZKP)
Non-interactive zero-knowledge proofs (NIZKP) are a variant of zero-knowledge proofs that do not require interaction between the tester and the verifier. In other words, the tester can send a single test to multiple verifiers so that they can verify it independently, without the need to repeatedly run the program to be tested.
This feature makes NIZKP very useful for distributed program review in large networks. Imagine, for example, that a company needs to check the integrity of a program running on thousands of devices on the company’s network. Instead of having to run the program on each device and manually review the results, the company could generate a single, non-interactive zero-knowledge test that can be sent to all devices on the network. Each device can then verify the test independently and without revealing confidential information.
In addition, NIZKP also offers the advantage of being more efficient than interactive zero-knowledge testing (IZKP). In interactive zero-knowledge testing, constant communication between the tester and the verifier is required, which can be time-consuming and costly. In non-interactive zero-knowledge testing, however, the test can be generated in advance and sent to the verifiers efficiently.
ZKP programming
In order to create zero-knowledge proofs (ZKP), it is necessary to use specialized programming languages to build the circuits and cryptographic protocols necessary for the creation of these proofs. Some of the most popular languages for creating ZKPs are listed below:
- Libsnark: It is a set of cryptographic libraries used for the creation of ZKP. It is compatible with different programming languages, including C++, Python and JavaScript, and is widely used in cryptography projects.
- Cairo: This is a programming language specially designed for the creation of ZKP. It is used to define the arithmetic circuits that are used to create zero-knowledge proofs. Cairo is a high-level programming language that facilitates the creation of zero-knowledge proofs.
- Circom: Another programming language specialized in the creation of zero-knowledge proofs. It is used to define arithmetic circuits and integrates with different cryptographic tools, such as snarkJS.
- Noir: This is a programming language for creating zero-knowledge proofs based on Rust. It is easy to use and has a large community of developers who contribute to its development.
- Leo: A programming language for creating zero-knowledge proofs that focuses on simplicity and ease of use. It is a high-level programming language that facilitates the creation of arithmetic circuits.
- Winterfell: A programming language used for creating zero-knowledge proofs on the Ethereum platform. It is used for creating arithmetic circuits that run on the Ethereum blockchain.
Unique features of ZKP
Zero Knowledge Proofing (ZKP) has become an important tool for ensuring privacy and security in various applications, such as identity management, electronic voting, financial transaction management, among others.
To implement these applications, specialized ZKP languages are used, which have some particular characteristics. On the one hand, these languages are relatively new and still under active development, which means that their use is limited to a few experts in the field. On the other hand, ZKP languages have special features not found in other conventional programming languages, such as their ability to handle zero-knowledge proofs and guarantee information privacy and security.
Although some ZKP languages such as Circom or Cairo are gaining popularity, there are still very few development tools available in these languages. This makes it difficult for programmers to work with these languages and may restrict access to a limited number of experts. In addition, ZKP languages are very difficult to audit due to the specialized nature of the languages and the complexity of zero-knowledge testing. This makes it difficult to verify the security and privacy of applications using these languages.
Despite these difficulties, ZKP languages are currently being employed to develop applications that handle large amounts of money, such as cryptocurrencies. This is because these languages offer a secure and private way of managing information, which is especially important in financial environments where privacy and security are paramount.
Vulnerabilities and threats
Although zero-knowledge proofs (ZKP) are a powerful tool for protecting privacy and information security, there are some problems associated with them:
– Computational complexity: Zero-knowledge proofs often require complex and costly computations in terms of computational resources. This may limit their applicability in some cases, especially on resource-constrained devices.
– Test validation: For a zero-knowledge test to be effective, its validity needs to be independently verifiable. This can be a challenge in some cases, especially if the proof is complex or if the collaboration of several parties is required.
– Cryptographic vulnerabilities: Zero-knowledge proofs rely on cryptographic protocols to ensure their security and privacy. However, these protocols may have vulnerabilities that can be exploited by attackers to compromise the security of the test.
– Threat model dependency: Zero-knowledge testing depends on the definition of the threat model, i.e. the assumptions made about potential attackers and their capabilities. If these assumptions are incorrect or incomplete, the security of the test can be compromised.
– Input privacy: One of the main advantages of zero-knowledge proofs is that they make it possible to prove that information is known without revealing it. However, this is not always possible, especially if the input is very limited. In such cases, it may be necessary to reveal part of the input in order to prove knowledge.
