Cryptography is a computer security discipline concerned with protecting the confidentiality, integrity and authenticity of information through encryption and decryption techniques. Its main objective is to ensure that transmitted information can only be read and understood by those authorised to do so, and cannot be accessed by unauthorised third parties. Cryptography is used in a wide variety of applications, from protecting military and government communications to securing online financial and commercial transactions. It is also used to protect the privacy of internet users, such as in the encryption of online communications and the secure storage of passwords.
There are different types of cryptographic algorithms used in cryptography, including symmetric key algorithms and public key algorithms. Symmetric key algorithms use the same key to encrypt and decrypt the message, while public key algorithms use a public and a private key pair to encrypt and decrypt the message.
General Scenario
The general cryptographic problem to be solved is the secure communication between two individuals, Alice and Bob, over an insecure channel in the presence of an adversary, Eve. The objective is to protect the confidentiality and integrity of the information transmitted, preventing Eve from being able to read or modify the message.
Cryptography provides tools to achieve this goal, and is based on the use of cryptographic algorithms that transform the original message into an encrypted message, which can only be read by the legitimate recipient in possession of the appropriate decryption key. The most common cryptographic algorithms are those based on symmetric key and public key.
In symmetric key cryptography, Alice and Bob share the same secret key, which they use for both encrypting and decrypting the message. However, the problem with this technique is that the key must be securely shared in advance, which can be complicated in some cases.
In public key cryptography, on the other hand, each user has a pair of keys, one public and one private. The public key is shared openly, while the private key is known only to the corresponding user. With this technique, Alice encrypts the message with Bob’s public key, and only Bob can decrypt it with his private key. This allows for more secure communication, without the need to share a secret key beforehand.
In any case, the main objective of cryptography is to ensure that the message sent by Alice reaches Bob securely and without being read or altered by Eve. To this end, cryptographic techniques are used to protect the confidentiality and integrity of the message, and additional measures such as authentication and digital signature are applied to guarantee the identity of the senders and receivers of the messages.
Objectives
Cryptography has several main objectives that focus on ensuring the security of transmitted information. The main objectives of cryptography are described below:
– Confidentiality: this objective focuses on ensuring that the content of the message is kept secret and is only accessible by the legitimate recipient. To achieve confidentiality, encryption techniques are used that transform the original message into an encrypted message that can only be understood by the authorised recipient who possesses the appropriate decryption key.
– Integrity: The objective of integrity is to ensure that the transmitted message is not altered during its transit from one point to another. To ensure integrity, hashing techniques are used, which generate a numeric value that represents the original message and allows any changes to the message during transmission to be detected.
– Authenticity: the aim of authenticity is to ensure that the source of information is legitimate and that the message has not been tampered with by a third party. To achieve authenticity, authentication techniques are used, such as digital signatures, which allow the receiver to verify the identity of the sender of the message.
– Signature: A digital signature is a technique used to bind certain information to the message. This ensures that the message has not been altered since the time it was signed, and that the sender of the message is who they say they are.
– Anonymity: this objective focuses on preserving the identity of the participants in a communication. To achieve anonymity, techniques such as encryption of the IP address, the use of anonymised networks and the use of public key cryptography to encrypt the identity of the participants are used.
Secret key cryptographic systems
Secret key cryptographic systems, also known as symmetric key cryptographic systems, are an encryption technique in which the sender and receiver share the same secret key to encrypt and decrypt messages. In this system, Alice and Bob share a private key K that is used to encrypt and decrypt messages.
When Alice wants to send a message to Bob, she uses the private key K to encrypt the message and sends the encrypted message over an insecure channel, such as the Internet. When Bob receives the encrypted message, he uses the same private key K to decrypt the message and read it in its original form.
One of the main benefits of secret key cryptographic systems is that they are fast and efficient. Because the same key is used to both encrypt and decrypt messages, the encryption and decryption process is fast and easy to implement. Moreover, these systems are highly secure as long as the secret key is kept confidential.
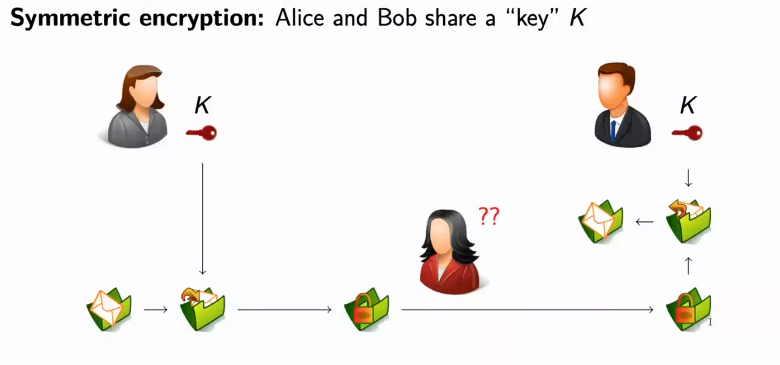
However, one of the main disadvantages of secret key cryptographic systems is the difficulty of sharing the secret key securely between Alice and Bob. This requires the existence of a secure communication channel between the two, which can be problematic in some situations. If an unauthorised third party, such as Eve, obtains the secret key, she can also decrypt the encrypted messages. For this reason, it is important to use secure key management techniques to protect the secret key and ensure the confidentiality of transmitted messages. These techniques include random key generation, secure key distribution using key exchange algorithms, mutual authentication of the parties and periodic key renewal.
In addition, even if the secret key is not intercepted, there is the possibility that Eve can reconstruct the key through cryptanalytic attacks. These attacks rely on the analysis of the cipher to infer information about the secret key. If Eve can reconstruct the secret key, then she can read the encrypted messages.
Another limitation of secret key cryptographic systems is that they are not suitable for digital signature. Digital signature is a cryptographic technique that allows Alice to authenticate a message and guarantee its integrity. In secret key systems, it is not possible to ensure the integrity and authenticity of the message independently, since both the sender and the receiver must share the same secret key.
Probabilistic Approach
The mathematical formalisation of cryptography is based on information theory and probability. In particular, the probabilistic approach is used to analyse the security of cryptographic systems.
The mathematical formalisation of the secret key cryptographic system is based on the notion of perfect security. An encryption system is perfectly secure if the original message and the encrypted message are statistically independent, i.e. if no information about the original message can be obtained from the encrypted message.
The mathematical relationship that formalises perfect security is the following:
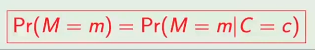
Where P(M) is the probability of the original message and P(M|C) is the probability of the original message given the encrypted message.
The above equation means that the probability of the original message does not change after it has been encrypted, i.e. the encrypted message does not provide any additional information about the original message. This property is known as perfect security and is the theoretical ideal for any cryptographic system.
However, it is important to note that perfect security is difficult to achieve in practice due to limitations in the generation of random numbers and the complexity of the algorithms used. Therefore, in practice, cryptographic systems are used that provide an acceptable level of security, but do not meet the property of perfect security.
Cryptographic key distribution
The distribution of cryptographic keys is a fundamental problem in secret key cryptography. In a multi-user system, each pair of users needs to have a different key in order to communicate securely. Therefore, if we want to increase the number of users in a network, the number of keys required increases exponentially, which becomes a scalability problem.
There are several methods to distribute cryptographic keys securely and efficiently. One of the most widely used methods is the Diffie-Hellman key exchange. This method allows two users to generate a securely shared key, even if Eve is listening in on the conversation.
The Diffie-Hellman key exchange works as follows:
- Alice and Bob agree on a set of integers and a large prime number p beforehand.
- They each choose a random secret number, a for Alice and b for Bob.
- Then, they each calculate a public number using the formula g^a mod p for Alice and g^b mod p for Bob, where g is a publicly chosen integer.
- Then, they exchange these public numbers.
- Finally, Alice and Bob calculate the shared key independently using the formula g^(a*b) mod p.
In this way, Alice and Bob can generate a securely shared key without the need to transmit it over an insecure communication channel.
Another method of distributing cryptographic keys is through the use of a key server. In this method, all users rely on a centralised server that maintains a database of cryptographic keys. Each user has a public key and a private key, and his public key is stored in the key server. When a user wants to send an encrypted message to another user, he obtains the recipient’s public key from the key server. The sender can then encrypt the message with the recipient’s public key and send it. Only the recipient can decrypt the message using his private key.
This method has the advantage that a private key does not need to be shared between individual users, which eliminates the need to constantly update keys. However, there is a security risk in that an attacker could attempt to attack the key server to obtain the users’ public keys and then decrypt the messages.
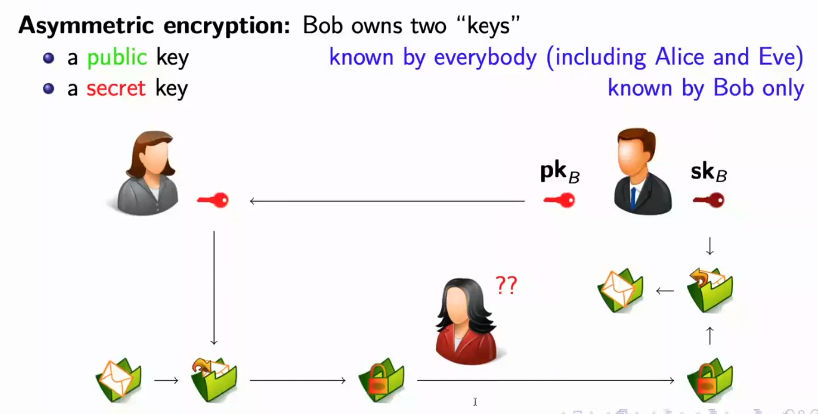
Public key cryptography
Public key cryptography, proposed in 1976 by Whitfield Diffie and Martin Hellman, is also known as asymmetric cryptography because it uses two different keys, one for encryption and one for decryption, whereas secret key cryptography uses the same key for both operations and is therefore symmetric.
One of the advantages of public key cryptography is that it allows the creation of digital signatures, which are essential for the authentication and integrity of messages. A digital signature is a code attached to an encrypted message that confirms that the message is from the sender it claims to be and that it has not been altered in transit. Public key cryptography is based on mathematical problems that are difficult to solve, such as the large number factorisation problem or the discrete logarithm problem. These problems are easy to pose, but very difficult to solve with current algorithms, which makes public key cryptography secure.
A common example of public key cryptography is the SSL / TLS protocol used in the encryption of secure connections on the web. When visiting a secure website, the server sends its public key to the user’s browser, which then uses that key to encrypt any information sent to the server. Only the server can decrypt the information using its private key.
Public key cryptography, also known as asymmetric cryptography, uses two different keys: a public key (e) and a private key (d). The public key can be shared freely, while the private key is kept secret. When someone wants to send an encrypted message to Bob, he first encrypts the message with Bob’s public key (e), which generates the encrypted message (C). Since Bob’s public key is known to everyone, anyone can encrypt a message to him. However, only Bob can decrypt the encrypted message, as he is the only one in possession of the private key (d) that is used to decrypt the message.
Original Message (M) + Bob’s Public Key (e) = Encrypted Message (C)
Encrypted Message (C) + Bob’s Private Key (d) = Original Message (M)
This public key scheme is commonly used for Internet security, such as in the secure transmission of sensitive information like credit card data, passwords and other private data. It is also used for authentication and digital signature, where the private key is used to sign a document and the public key is used to verify the authenticity of the signature.
The padlock analogy is a good way to understand the concept of public and private key. The public key can be shared widely, like the padlock that is available to anyone who wants to lock it. However, only the person who has the corresponding private key can open the lock or decrypt the message. It is as if the owner of the lock has a special key that only he or she possesses and can only use to open the lock.
As for the idea of the public key as an address, it is similar to how people can send mail to a specific address without having access to the key to the door. The public key is the address to which the message is sent and the private key is the key used to open the message. Thus, the public key acts as an access point so that anyone can securely send messages to the correct recipient, while the private key ensures that only the actual recipient can access the message.
Cryptography and Business
Finally, it is necessary to show that there are many companies and protocols that use cryptography. Here are some examples:
– AES (Advanced Encryption Standard): is a block cipher algorithm used to protect sensitive information. AES is considered one of the most secure cryptographic algorithms and is widely used in information security applications.
– RSA (Rivest-Shamir-Adleman): is an asymmetric encryption algorithm used to encrypt and digitally sign information. RSA is based on number theory and is used in information security applications such as SSL, SSH and PGP.
– SHA-2 (Secure Hash Algorithm 2): is a family of cryptographic hash algorithms used to verify the integrity of information. SHA-2 is considered one of the most secure hash algorithms and is used in applications such as password authentication and file verification.
– Blowfish: is a symmetric block cipher algorithm used to protect sensitive information. Blowfish is considered one of the fastest and most secure algorithms and is used in applications such as password protection and file encryption.
– ECC (Elliptic Curve Cryptography): is an asymmetric encryption algorithm that uses elliptic curves instead of integers to generate cryptographic keys. ECC is considered more efficient and secure than traditional encryption algorithms and is used in applications such as mobile device security and password authentication.

Good Work! 🙂
The amount of effort that you put into it was very impressive to observe. Despite the fact that the picture is appealing and your writing style is elegant, it appears that you are concerned about the fact that you ought to be providing the following content. In the event that you take care of this hike, I will almost definitely return to come back and read more of your work.
I have found your analysis of applied cryptography to be very educational. Is there any book or additional resource you would recommend?
Thank you for sharing such valuable information! Would you consider doing webinar on this topic?
Your posts in this blog really shine!